In the vast digital landscape, the line between genuine content and sponsored material often blurs, especially when Potentially Unwanted Programs (PUPs) come into play. These programs, particularly search toolbars, have mastered the art of integrating sponsored content and links into users’ daily browsing experiences. This article delves deep into this Continue Reading
Base
Mobile Websites Versus Mobile Apps: What Are The Best Approach to Business Development
“Do I need an app?” or “Can I just build a mobile website?” — these are the two questions entrepreneurs struggle to answer when launching their businesses. The central point in making this decision is price. Speed, stand-alone access, and maintenance also significantly contribute to decision-making. However, it can be Continue Reading
Dating App Development in 2023: Everything You Need to Know
In a global pandemic, when the majority is sitting in the comfort of their apartments, the need for communication is felt more than ever. And against this background, the popularity of various dating applications is growing rapidly. Analysts estimate that global dating app revenue exceeded $3.08 billion in 2020. This Continue Reading
Dealing with Software Database Issues
A database is no less than the heart of any software solution. It’s a critical element whose potential issues can considerably affect the operation, performance, and overall security of your software. Understanding these issues becomes an indispensable requirement for everyone in the software development or management industry, including entrepreneurs, developers, Continue Reading
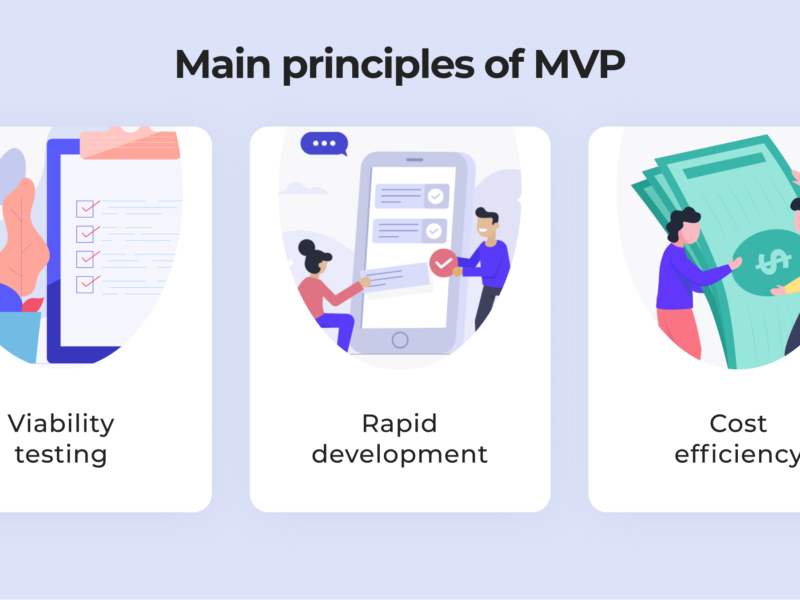
How to Benefit From Minimum Viable Products at the Start of Your Business?
Applications often begin with MVP. Minimum viable product is used by app developers and entrepreneurs at the dawn of a digital product’s creation. First of all, MVP is essential to test the app’s usability to prevent going far on the path of development with a serious flaw in the pocket. Continue Reading
Why do we need a database for the site?
As I noticed, not everyone understands and knows why the site needs a database, and in general whether he needs it? The question is interesting enough because not all sites need it, and some without it at all how can not cope. In this article I would like to analyze Continue Reading
Why you need to learn more about database
The database is at the center of the modern software. Most of the software being written today uses databases. Nothing in software is more universal, or more central to everything. Databases have three important characteristics. First, they are huge. Almost everything ever written is stored in a database. Databases hold Continue Reading
ACID transactions
Actions with data that have the properties of atomicity, consistency, isolation and Durability is the ACID definition of a transaction. D – Durability is the same model I was talking about: if the data has already been written to disk, then we believe that it is there, recorded securely and Continue Reading
Proficiency in code
There is an interesting story in German road traffic regulations. If the road narrows, then the rules prescribe to get to the end, and only then rebuild one by one, and the neighboring car must let through. All are rearranged strictly one after another – this sign speaks about it. Continue Reading
Storage layers
Let’s start with the storage layer. Understanding how it works helps to understand what is happening on the higher layers. The storage layer provides: ✓ Concurrency and efficiency. In other words, it is competitive access. That is, when we try to benefit from concurrency, the problem of concurrent access inevitably Continue Reading